Data integrity, the main feature of a well-functioning business, is not merely a buzzword. If you consider it, then all your decisions, reports and strategies will rely on data that is correct and coherent. A single wrong data point or contaminated record can cause expensive mistakes. The quality of your data is not a mere question of technology; it is a smart business decision that fortifies your operations and guarantees your progress.
However, data integrity is not always guaranteed, especially in the course of system changes or technological innovations. The cloud offers to be a good partner in providing flexibility, scalability and efficiency, but, at the same time, it can be a bad partner by exposing your data to security threats. Therefore, it is very important to understand the link between integrity and cloud security, as it is going to define your data management approach. Your data needs to be accurate, consistent and safe, no matter where it resides.
After going through this guide, you will be in a position to know how to migrate to the cloud without losing your data, bypass the common mistakes and, finally, establish practices that not only keep your business safe but also quick. Do not let a data error be the reason for you to act; be the one to control your data and secure your cloud journey now. Your business is worth it.
What is a Cloud Migration?
Cloud migration is defined as the movement of business applications, data, and workloads from on-premises to cloud infrastructure and services. In other words, it is like moving to the digital online office where all features such as access, flexibility, and scalability are already built into the building. For instance, public cloud migration was one of the main reasons why big companies like Netflix, Dropbox, etc., were able to grow fast; still, in 2025, about 94% enterprises worldwide will use cloud computing in some form.
The process of migration does not only mean the relocation of data, but it also allows for real benefits to the business. In addition, the supply of cloud resources can be easily varied according to the needs. For example, both large and small companies are moving towards cloud computing for their workloads to manage peak demands smartly. As per the latest statistics, more than 60% of the data generated by companies is now kept on the cloud.
On the other hand, the migration to the cloud does bring some risks along with it unless you have a very good plan in place. Cloud data security best practices in the cloud need to be implemented for control of the confidentiality of data, for example, encryption, access management, and monitoring to prevent unauthorised access.
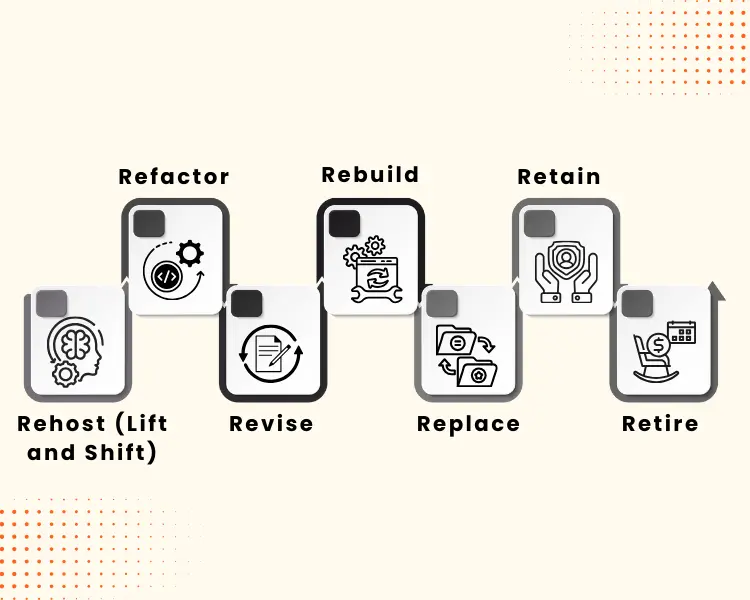
What are the 7 R's of Data Migration?
At the time of a data move, Data Integrity is a very important issue that needs to be guaranteed, which means the data should be accurate, uniform, and whole. The 7 Rs tool is one of the most effective techniques to choose the right data migration method through which:
- Rehost (Lift and Shift)
There is no requirement to modify the architecture. Just transfer the database and apps to the cloud. This is a quick and simple process. To illustrate, the old CRM system can be migrated to the cloud virtual machine with no code refactoring required. - Refactor
The cloud’s features, such as auto-scaling or managed services, can be utilised by performing minor modifications to your application while retaining the main functionality. This will promote both Cloud Compatibility and Integrity. - Revise
Make major changes to the system, which will have a positive impact on performance or security. For instance, splitting a single application into a number of services according to their function for a more efficient cloud infrastructure use. - Rebuild
Start anew by building the application on the cloud. A brand-new architecture is the result of non-compatibility or ageing of legacy systems, and this architecture is clean, efficient, and future-proof at the same time. - Replace
Switching from an on-premise inventory management tool to a SaaS product that runs in the cloud, for instance, makes it possible to save on maintenance costs by moving from an in-house to a cloud-native inventory management tool. - Retain
A hybrid environment is formed when certain workloads are kept on-premises for reasons such as compliance, latency, or regulation, while other workloads are being transferred to the cloud. - Retire
Decommission those systems that are redundant or have already been replaced. The reduction of legacy systems that are not needed lowers the risks and complexities associated with security, thus facilitating the secure cloud data storage when old data is either archived or deleted.
Step-by-Step Guide: Cloud Migration Security
In order to mitigate the risks, the first action is going to be an audit of your data, applications and processes, which will be comprehensive. Research indicates that poor controls are the reason for around 60% of cloud migration security breaches; thus, it is very important that a security strategy is planned.
Completely knowing your resources, you can select the most suitable (public, private, or hybrid) cloud deployment model that will comply with your legal obligations, uphold your performance standards and budgetary restrictions.
The process of moving to a secure cloud begins with a thorough examination of your data, applications, and processes in order to pinpoint the assets, classify the sensitive data, and establish the dependencies. From there, you can decide which cloud model is the best fit—either public, private, or hybrid—that will meet your needs in the areas of security, compliance, performance, and budget.
What are the Major Risks to Data Quality During Migration?
Even with a good strategy, migration might still bring about data quality issues. One of the biggest hazards is misconfiguration: incorrect data mapping or migration scripts may lead to disfigured records, duplicates, or omissions. Such a situation can have a severe impact on business activities.
For example, some firms have even declared the complete loss of important documents after a migration process, which then necessitated the use of expensive methods to recover them, waiting that takes even longer than expected, or even more disgruntled customers.
Moreover, one more risk is related to mistakes made by the staff and a lack of control. Recent research has shown that over half of the cloud migration security challenges can be attributed to errors in configuration and human mistakes. If carelessness is applied to the handling of roles, permissions, or encryption settings, then it might happen that sensitive data will go out in the open or will be lost forever.
Is Your Cloud Strategy Ready for an AI-Driven Scale?
For your cloud journey to be secure and durable, it would be prudent to do a thorough risk assessment for cloud migration at the very beginning.
- Adopt a hybrid approach: Mixing up with different suppliers and relying less on one vendor will help ease the impact of any security incident since the workload is shared among different parties.
- Regularly update security protocols: The best of all security controls, encryption techniques, and access rights should be applied.
- Train your personnel: Mistakes made by humans account for the majority of security incidents. With the training provided, the people will be well-versed in cloud best practices, and thus, errors will significantly decrease.
- Use automation wherever it is applicable: Validation, backup, compliance check, etc., should all be automated. The result will be fewer human mistakes, and the quality of the results will remain the same.
Conclusion
The protection of data integrity is not merely a technical necessity but the foundation of every triumphant cloud migration plan. The modernisation of your systems leads to the big advantage of providing a guarantee that your data will be accurate, unaltered, and totally trustworthy throughout all stages.
Here is where Revolution AI comes in as your strategic partner by not only assisting you with the installation of high-end cloud security infrastructures but also by providing automation for real-time tracking, making compliance-connected plans, and offering universal protection customised to your environment. Want to create a reliable cloud-based solution? Contact Revolution AI Today, and we will safeguard your cloud transformation step by step.
Frequently Asked Questions
Many teams underestimate the complexity involved. Issues like misconfigured settings, incompatible systems, and unclear data ownership often slow things down. With proper planning and early testing, most of these challenges can be avoided.
The most effective way is to validate data before, during, and after the migration. This includes running integrity checks, comparing old and new datasets, and using automated tools to detect mismatches or missing information.
Cloud environments move fast. New workloads, users, and permissions get added frequently, which creates more entry points for attackers. Without strong visibility and round-the-clock oversight, threats can stay hidden longer than expected.
If the migration involves sensitive data, strict compliance rules, or large-scale applications, expert support can prevent costly mistakes. Specialists ensure your systems are configured correctly and help you avoid risks that may not be obvious at first glance.

Hemal Sehgal
Introducing Hemal Sehgal, a talented and accomplished author with a passion for content writing and a specialization in the blockchain industry. With over two years of experience, Hemal Sehgal has established a strong foothold in the writing world, c...read more